PCI DSS, which stands for Payment Card Industry Data Security Standard, is essentially the global rulebook for handling credit card data safely. It's a mandatory set of security rules created by the major card brands to keep customer information out of the hands of fraudsters and thieves.
Understanding PCI DSS and Its Importance

Think of PCI DSS as the minimum safety code for your business's payment infrastructure. It's not a law passed by a government, but it might as well be. Any business that accepts, processes, stores, or transmits cardholder information is required to follow these technical and operational standards. This applies to everyone, from a global SaaS platform to a small online shop.
The main goal here is straightforward: create a secure environment to protect sensitive card data every single time a customer hits "buy." This shield protects your customers from identity theft and protects you, the merchant, from the devastating fallout of a data breach.
Who Creates and Enforces These Rules?
The standards themselves come from the PCI Security Standards Council (PCI SSC). This council was founded by the five major card brands you know well: Visa, Mastercard, American Express, Discover, and JCB.
But here's a key distinction: the Council creates the rules, but they don't enforce them. Enforcement is handled by the individual card brands and the acquiring banks, the financial institutions that process your transactions. If you fall out of compliance, they're the ones who will come knocking with penalties.
Why It's More Than Just a Checklist
It’s easy to look at PCI DSS as just another list of boxes to tick, but that mindset misses the point entirely. At its core, compliance is about building and maintaining trust with your customers. When someone feels confident that their payment details are safe with you, they're far more likely to complete that purchase and come back for more.
Following these standards does more than just keep the card brands happy. It helps your business:
- Prevent Costly Data Breaches: A secure system is your best defense against attacks that could expose sensitive customer data and cripple your business.
- Build a Strong Reputation: Showing customers you take their security seriously is a powerful way to demonstrate that you value their privacy and business.
- Avoid Significant Penalties: Non-compliance can lead to massive fines, higher transaction fees, and in the worst-case scenario, having your ability to accept card payments revoked.
- Improve Overall Security: The requirements push you to adopt smarter security habits across the board, protecting your entire business, not just payment data.
The latest version, PCI DSS 4.0, really ups the ante with 64 new requirements. Of those, 51 become mandatory on March 31, 2025. The cost of ignoring these rules is no joke, as fines often start at $5,000 per month and can escalate quickly for ongoing issues. You can dig into a more detailed analysis of PCI DSS compliance facts to prepare for what's ahead.
The 12 Core Requirements of PCI DSS Explained
Staring at the 12 core requirements of PCI DSS can feel like trying to decipher a dense legal text. It’s overwhelming. But here's a much better way to think about it: the rules are grouped into six logical goals.
Instead of a random checklist, picture it as layers of security, with each rule building on the last to create a rock-solid defense for cardholder data. Let's walk through these goals and see how the specific requirements fit in, using real-world analogies to make sense of it all.
Goal 1: Build and Maintain a Secure Network
This is the foundation of everything. It's about building a strong digital perimeter around your systems. Think of it as constructing a fortress with a single, heavily guarded gate that controls all traffic coming in and out.
- Requirement 1: Install and Maintain Network Security Controls: In simple terms, this means firewalls. A firewall is your digital bouncer, inspecting every bit of traffic and turning away anything that looks suspicious. It’s the first line of defense, ensuring only trusted connections can talk to the systems handling sensitive payment data.
- Requirement 2: Apply Secure Configurations to All System Components: Never trust the defaults. This rule is about changing all vendor-supplied settings, like the classic "admin/password," and stripping out any unnecessary software from your servers and devices. It’s the digital equivalent of rekeying the locks on a new house; you wouldn't trust the factory-set ones, would you?
Goal 2: Protect Stored Account Data
If you absolutely have to store cardholder data, you need to make it completely unreadable and useless to anyone who might steal it. This goal is all about treating that data like a state secret.
- Requirement 3: Protect Stored Account Data: The golden rule here is simple: if you don't need it, don't store it. If you must keep card data, it has to be unreadable through methods like encryption, truncation (masking most of the digits), or tokenization, which swaps the real data for a non-sensitive placeholder.
- Requirement 4: Protect Cardholder Data with Strong Cryptography During Transmission: When card data travels across the internet, it's out in the open and incredibly vulnerable. This requirement mandates using strong encryption like TLS (Transport Layer Security). This wraps the data in a secure tunnel, which is what that little padlock icon in your browser signifies. No one can eavesdrop on the conversation.
Goal 3: Maintain a Vulnerability Management Program
What's secure today could have a gaping hole in it tomorrow. This goal is about staying on your toes, constantly watching for new threats, and patching up weaknesses before attackers can find them.
- Requirement 5: Protect All Systems and Networks from Malicious Software: This is your antivirus and anti-malware mandate. These tools need to be running on all your systems and, just as importantly, kept constantly updated to catch the latest viruses, spyware, and other nasty code.
- Requirement 6: Develop and Maintain Secure Systems and Applications: Security can't be an afterthought bolted on at the end. This means applying security patches from vendors the moment they're available and ensuring any custom code your team writes is built from the ground up with security in mind.
Key Takeaway: A shocking number of data breaches happen because of unpatched systems. Vulnerability management isn't just a compliance box to tick; it's a fundamental business practice that prevents attacks you really should have seen coming.
Goal 4: Implement Strong Access Control Measures
Let’s be honest: not everyone on your team needs to see customer credit card numbers. This goal is all about locking things down so only the right people can access sensitive systems, and you can prove who did what.
- Requirement 7: Restrict Access to Cardholder Data by Business Need-to-Know: This is the "principle of least privilege." Access to card data should only be given to employees whose job is impossible without it. For everyone else, the door is closed and locked by default.
- Requirement 8: Identify and Authenticate Access to System Components: Every single person needs their own unique login. This rule kills shared accounts (like a team-wide "admin" login) and demands strong authentication like complex passwords and, increasingly, multi-factor authentication (MFA).
- Requirement 9: Restrict Physical Access to Cardholder Data: Your digital security is useless if someone can just walk into your server room and unplug a hard drive. This requirement covers the physical world: locked doors, security cameras, and secure storage for any paper documents with card numbers on them.
Goal 5: Regularly Monitor and Test Networks
You can't protect what you can't see. This goal is about having your eyes open, continuously watching for suspicious behavior, and proactively testing your defenses to make sure they actually work.
- Requirement 10: Log and Monitor All Access to System Components and Cardholder Data: You need to keep a detailed activity log for your network, tracking every touchpoint with cardholder data. More importantly, someone needs to review these logs regularly to spot the subtle signs of a potential breach.
- Requirement 11: Test Security of Systems and Networks Regularly: This isn't a "set it and forget it" system. It involves running routine vulnerability scans with an Approved Scanning Vendor (ASV) and hiring experts to perform penetration tests, which are ethical hacks designed to find weaknesses just like a real attacker would.
Goal 6: Maintain an Information Security Policy
Finally, all of this needs to be written down. A formal policy connects all these moving parts and ensures everyone in the company is on the same page.
- Requirement 12: Support Information Security with Organizational Policies and Programs: This is the master plan. You need a comprehensive, documented security policy that is shared with all relevant staff and reviewed at least once a year. It's the playbook that guides your entire security strategy.
Why PCI DSS Compliance Is a Business Superpower
It's easy to see PCI DSS compliance as just another box to check, a tedious chore on a long to-do list. But that view misses the bigger picture. Smart businesses treat compliance as a strategic advantage, a real superpower that pays off long after the audit is done. Think of it as a foundational investment in your company's growth and your customers' loyalty.
At its heart, compliance builds something you can't buy: customer trust. Every time someone types their card details into your checkout form, they're trusting you to keep their information safe. A solid compliance posture isn't just about passing a test; it's a clear signal to your customers that you take their security seriously. That confidence often leads directly to better conversion rates and more repeat business.
The Tangible Benefits of Strong Compliance
Beyond building trust, the discipline required for PCI DSS actually strengthens your entire security setup. The process forces you to look closely at your systems and often reveals vulnerabilities you never knew existed, protecting not just cardholder data but all of your company's sensitive information.
- Boost Your Brand Reputation: When you can prove you’re committed to security, you instantly stand out from competitors who cut corners. It becomes a powerful part of your brand identity.
- Build Resilient Operations: PCI DSS requires regular monitoring, testing, and maintenance. This creates a much more robust and reliable infrastructure, significantly lowering the risk of costly downtime from a security incident.
- Lay the Groundwork for Growth: If you have ambitions to sell internationally, PCI compliance is non-negotiable. It’s a globally recognized standard that opens doors to new markets, payment processors, and partnerships worldwide.
Seeing how PCI DSS fits into a broader compliance context helps you appreciate its role in a holistic cybersecurity strategy.
The Harsh Realities of Non-Compliance
On the flip side, ignoring or half-heartedly approaching PCI DSS can have devastating consequences. The risks are far more severe than a simple slap on the wrist. This is one corner you absolutely cannot afford to cut.
The financial penalties alone can be crippling. The major card brands can levy fines ranging from $5,000 to $100,000 per month for violations. And those direct fines are often just the tip of the iceberg.
The real damage comes after a data breach. On top of fines and forensic investigation costs, the hit to your reputation can destroy customer trust for years, crippling future sales. The worst-case scenario? Losing your merchant account entirely, which means you can no longer accept card payments.
The stakes are only getting higher. The PCI compliance software market is expected to hit $6,500 million by 2025, a clear sign of how critical this has become. A data breach linked to non-compliance costs a business an average of $174,000 extra per incident, pushing the total average cost to an eye-watering $4.61 million. You can dig deeper into these numbers by exploring insights on the PCI compliance software market.
For any modern business, compliance isn't a burden. It's a fundamental pillar supporting a healthy, secure, and trustworthy operation. It’s the superpower that protects your customers, your reputation, and ultimately, your bottom line.
A Look at the Key Changes in PCI DSS 4.0
The rules for protecting payment card data aren't set in stone. They have to change to keep up with new threats, and the recent move to PCI DSS 4.0 is a big one. This isn't just a minor update; it's a fundamental shift in how we think about payment security.
If you think of the old standard as a rigid, paint-by-numbers checklist, version 4.0 is more like a professional blueprint. It still defines the end goal, a secure payment environment, but it gives businesses more flexibility in how they get there. You're no longer forced to use a specific tool if you can prove an alternative, customized control meets the security objective just as well, or even better.
This change is a direct acknowledgment that a one-size-fits-all security plan just doesn't cut it anymore. By allowing for customized controls, the new framework encourages companies to build security practices that are tailored to their specific risks and can adapt as new threats emerge.
Core Updates You Need to Know
PCI DSS 4.0 brings a lot to the table, but a few new requirements really stand out. They’re designed to patch up some of the most common security holes that attackers love to exploit.
Here’s where the focus has sharpened:
- Stronger Multi-Factor Authentication (MFA): MFA is no longer just for the people with the admin keys. It’s now required for any access into the cardholder data environment. This makes it significantly harder for a bad actor to get in, even if they manage to swipe a password.
- Targeted Phishing Awareness: Gone are the days of generic, once-a-year security training. The new standard demands training that specifically covers the latest phishing tactics and social engineering scams. It’s all about turning your team into a smarter, more vigilant first line of defense.
- Protection Against Digital Skimming: To fight back against attacks that inject malicious code onto checkout pages, there are new rules. Businesses now have to actively manage all scripts running on their payment pages and have technical controls in place to spot and block unauthorized changes.
The Clock is Ticking: PCI DSS 4.0 is already here, but organizations were given a grace period to get their house in order. That window is closing. All the new requirements become mandatory for everyone on March 31, 2025.
The March 2025 Deadline and What It Means
That date isn't a friendly suggestion, it's a hard stop. By March 31, 2025, all 51 of the new, "future-dated" requirements in PCI DSS 4.0 must be fully implemented.
This isn't just about ticking a few new boxes. We're talking about major new controls, like actively managing payment page scripts to prevent web-based skimming attacks, implementing automated tools to protect public-facing web applications, and enforcing even stricter encryption for data on the move.
This shift is part of a bigger trend. We're seeing more businesses adopt comprehensive security frameworks, with 81% of organizations also working toward ISO 27001 certification to bolster their defenses. You can dig into more of the latest compliance statistics and trends to see the bigger picture. Getting a handle on these changes now is the only way to make sure your business stays compliant and genuinely secure.
A Practical Roadmap to Achieving Compliance
Getting started with PCI DSS compliance can feel overwhelming. But if you break it down, it's a logical journey that starts with understanding your own payment environment and ends with building a lasting security culture. This isn’t a one-and-done project; it's an ongoing promise to protect your customers and your business.
The first, most critical step is to define your compliance scope. Think of it as drawing a protective border around everything that touches cardholder data. Your scope includes every server, application, network, and even every person who could potentially affect the security of that sensitive information.
Here’s a simple truth: the smaller you can make your scope, the easier, faster, and cheaper your compliance journey will be.
Once you have that map drawn, it's time to validate your security. For most small to medium-sized businesses, this is handled with a Self-Assessment Questionnaire (SAQ). This is basically a checklist you use to report on your security posture to your acquiring bank and the card brands.
Understanding the Self-Assessment Questionnaire
The SAQ isn't just one form. It's a whole family of questionnaires, each designed for a specific way of handling payments. Choosing the right one is essential because picking the wrong one means wasting a ton of time and effort on requirements that don’t even apply to you.
There are several versions, but some are much more common than others. For instance, a merchant that completely outsources its payment processing to a compliant partner will have a much shorter, simpler SAQ than a company that stores card data on its own servers. It’s all about matching your business model to the right questionnaire.
Common Self-Assessment Questionnaire (SAQ) Types
To help you get a better idea, let's break down the most common SAQ types. Think of this as a cheat sheet to help you find your starting point.
.tbl-scroll{contain:inline-size;overflow-x:auto;-webkit-overflow-scrolling:touch}.tbl-scroll table{min-width:600px;width:100%;border-collapse:collapse;margin-bottom:20px}.tbl-scroll th{border:1px solid #ddd;padding:8px;text-align:left;background-color:#f2f2f2;white-space:nowrap}.tbl-scroll td{border:1px solid #ddd;padding:8px;text-align:left}SAQ TypeWho It's ForExample Use CaseSAQ AMerchants who have completely outsourced all cardholder data functions to compliant third-party service providers. Cardholder data is never processed, stored, or transmitted on their own systems.An online store using a fully hosted checkout page from a payment processor like Suby, where the customer is redirected to the processor's secure page to enter their card details.SAQ A-EPE-commerce merchants who partially outsource payment processing but whose websites can still impact the security of the payment transaction.A business that uses a direct post method, where the payment form is on their website, but the data is sent directly from the customer's browser to the payment processor.SAQ DAny merchant who does not meet the criteria for any other SAQ type. This is the most comprehensive and demanding questionnaire, covering all PCI DSS requirements.A larger business with complex in-house systems that store, process, and transmit cardholder data, requiring a full validation of all 12 core requirements.
Choosing the right SAQ can be the difference between a few days of paperwork and a months-long technical audit. If you want to dive deeper into how different payment setups influence these requirements, our guide on integrating a payment gateway API explains how it can dramatically simplify your compliance burden.
Ongoing Validation and Maintenance
PCI compliance isn't a destination; it's a continuous process. You don't just "get compliant" and move on. It's a cycle of assessing your defenses, fixing any weaknesses, and reporting your status. Beyond the SAQ, two other key elements often come into play.
- Vulnerability Scans: If your business has any external-facing IP addresses in your scope (like a web server), you'll need to run quarterly vulnerability scans. These aren't just any scans; they must be performed by an Approved Scanning Vendor (ASV), which is a company certified by the PCI SSC to hunt for security weaknesses.
- Qualified Security Assessors (QSAs): For larger merchants, typically Level 1, an SAQ isn't enough. They need a full, on-site audit conducted by a QSA. These independent security experts perform a deep-dive into your entire environment and produce a formal Report on Compliance (ROC).
This flowchart illustrates some of the key changes and areas of focus in the latest PCI DSS 4.0 standard.
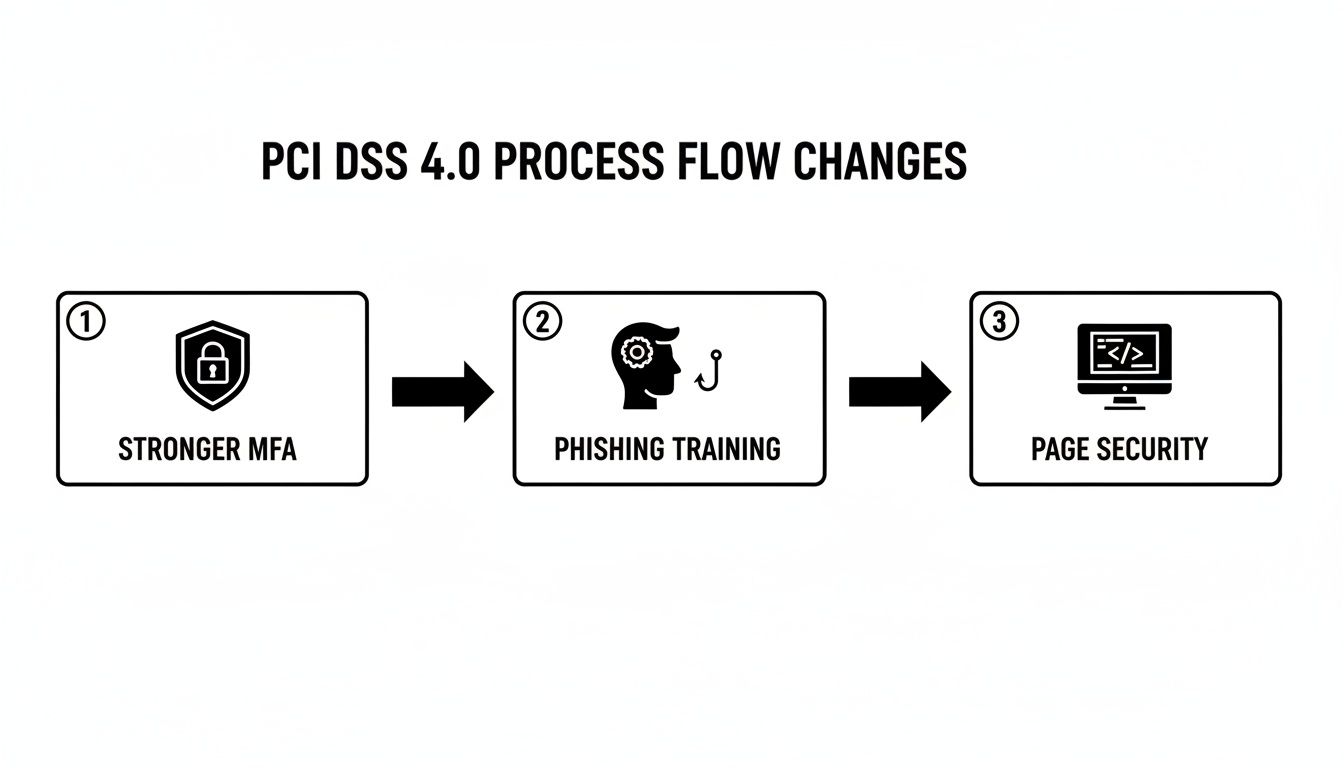
As you can see, the new standards are pushing for a more proactive defense against modern threats like phishing and attacks that target the customer's browser.
Continuous Compliance is the Goal: Security is a moving target. New threats pop up constantly, and your own systems are always evolving. True compliance means embedding security into your daily operations through ongoing monitoring, regular staff training, and periodic reviews to make sure your defenses always hold up.
The Smartest Way to Simplify Your PCI Compliance
Trying to tackle PCI DSS compliance on your own can feel like an impossible task. But here’s the secret: the most effective strategy isn't about mastering every single rule. It’s about intelligently minimizing the number of rules that apply to your business in the first place. This is what we call reducing your compliance scope.
The logic is beautifully simple. The fewer of your systems that touch, transmit, or store sensitive cardholder data, the smaller your security burden becomes. Think of it like building a secure vault. By outsourcing the handling of the most valuable assets, the payment details, you shrink the size of the vault you personally need to guard and audit.
How Outsourcing Slashes Your Scope
Using a PCI DSS Level 1 certified payment solution is, without a doubt, the single best way to reduce your scope. Instead of trying to build a fortress-like payment infrastructure from the ground up, you're partnering with an expert who has already built one.
When you integrate a secure payment processor, your business never directly handles raw credit card information. The entire responsibility for capturing, transmitting, and protecting that data is shifted to your provider, who manages it within their own heavily-fortified environment. For your own compliance work, this is a total game-changer.
Your number one goal should be to keep cardholder data as far away from your own servers and applications as possible. The instant that data touches your systems, your compliance responsibilities explode.
This strategy frees you up to focus on what you actually do best, building your product and delighting your customers, without the constant distraction of complex security audits.
A Practical Example of Scope Reduction
Let's see what this looks like in the real world. When you integrate a payment solution like Suby, whether through its flexible API or native integrations for platforms like Discord and Telegram, you're essentially offloading the entire security risk.
- Hosted Checkout Pages: Your customer types their card details directly onto a secure page hosted by the payment provider. That sensitive data never even grazes your servers.
- API Integrations: Data is sent straight from the customer’s browser to the provider’s secure servers, completely bypassing your systems.
This approach immediately removes your infrastructure from the direct flow of cardholder data. For most businesses, this simplifies the entire compliance process down to filling out the shortest and easiest Self-Assessment Questionnaire, SAQ A. This form is basically just you confirming that you’ve fully outsourced all payment functions to a compliant third party.
By taking this path, you can confidently how to accept credit card payments from a global audience. Businesses can receive their payouts in USDC, while their customers enjoy the simplicity of paying by card. This gives you all the upside of a worldwide payment system without the operational headache and financial risk of managing a massive PCI DSS program.
Still Have Questions? Let's Clear Things Up
PCI DSS can feel like a maze of rules and requirements. Here are some plain-English answers to the questions we hear most often from business owners and developers.
We Only Process a Handful of Payments. Do We Get a Pass?
Unfortunately, no. There’s no "too small to comply" clause in the PCI DSS rulebook. If your business accepts, handles, or even just touches cardholder data in any way, the standards apply to you.
It doesn't matter if you process ten transactions a month or ten thousand a day. The core responsibility to protect that customer data is exactly the same. What does change is the complexity of your compliance validation; smaller businesses typically have a much simpler path.
But We Use a Big-Name Payment Processor. Aren't They Handling It?
Yes and no. Using a compliant third-party processor like Stripe or PayPal is a massive help, but it doesn't get you completely off the hook. Think of it this way: they're responsible for their own security, but you're still responsible for yours.
Outsourcing your payment processing is the single smartest move you can make. It dramatically shrinks your "compliance footprint," often reducing your job to filling out the simplest Self-Assessment Questionnaire. This is why partnering with a Level 1 provider is a non-negotiable best practice.
Is Our SSL Certificate Good Enough for PCI Compliance?
An SSL/TLS certificate is absolutely essential, but it’s only one ingredient in a much larger recipe. It handles Requirement 4 by encrypting data as it travels between your customer's browser and your server, but that's it.
True PCI compliance means addressing all 12 requirements, which cover everything from firewall configuration and access control to how you screen new hires. An SSL certificate is a great start, but it doesn't even begin to cover the rest of the security measures you need in place.
Can We Just Store Credit Card Numbers for Subscriptions?
Technically, you can, but you really, really shouldn't. Storing raw credit card numbers on your own systems is like choosing to keep a pile of cash on your desk instead of putting it in a bank vault. It instantly skyrockets your risk, liability, and the intensity of your PCI compliance requirements.
The modern, secure way to handle this is through tokenization. Your payment provider can take the sensitive card data and give you back a unique, non-sensitive "token." You can safely store and use that token for recurring billing without ever having the actual card number on your servers.
Ready to simplify your global payments and slash your PCI compliance burden? With Suby, you can accept card payments worldwide and get settled directly in USDC. Our secure, API-driven checkout handles the heavy lifting, so you can get back to building your business. Get started with Suby today.


